The Clock is Ticking: Why Government Contractors Must Act Now for CMMC Compliance

ⓘ Update (September 2025): New CMMC Deadline Announced
The Department of Defense has announced that new CMMC 2.0 cybersecurity requirements will officially take effect on November 10, 2025.
While this shifts the original deadline, the core message of this article remains unchanged: the time to act is now. The path to compliance—from readiness assessments to remediation and documentation—is a significant undertaking that cannot be completed overnight.
We urge you to use the information below to assess your firm’s position and take decisive action to protect your future DoD contracts.
For government contractors in the architecture, engineering, and construction (AEC) industry, cybersecurity compliance is no longer an option; it’s a requirement. The Department of Defense’s (DoD) Cybersecurity Maturity Model Certification (CMMC) 2.0 framework is set to take effect on November 10, 2025, and failing to meet its standards could mean losing valuable federal contracts.
If your firm handles Controlled Unclassified Information (CUI) as part of government projects, compliance with CMMC 2.0 Level 2 and NIST 800-171 is mandatory. With the deadline fast approaching, now is the time to assess your cybersecurity posture and take the necessary steps to ensure compliance. Waiting until the last minute will put you at risk.
What is CMMC 2.0 and Why Does it Matter?
CMMC 2.0 is the DoD’s response to growing cybersecurity threats, designed to protect sensitive government data across the defense industrial base. This updated framework simplifies compliance by consolidating security requirements into three levels, with Level 2 aligning directly with NIST 800-171, a set of security controls that all contractors handling CUI must follow.
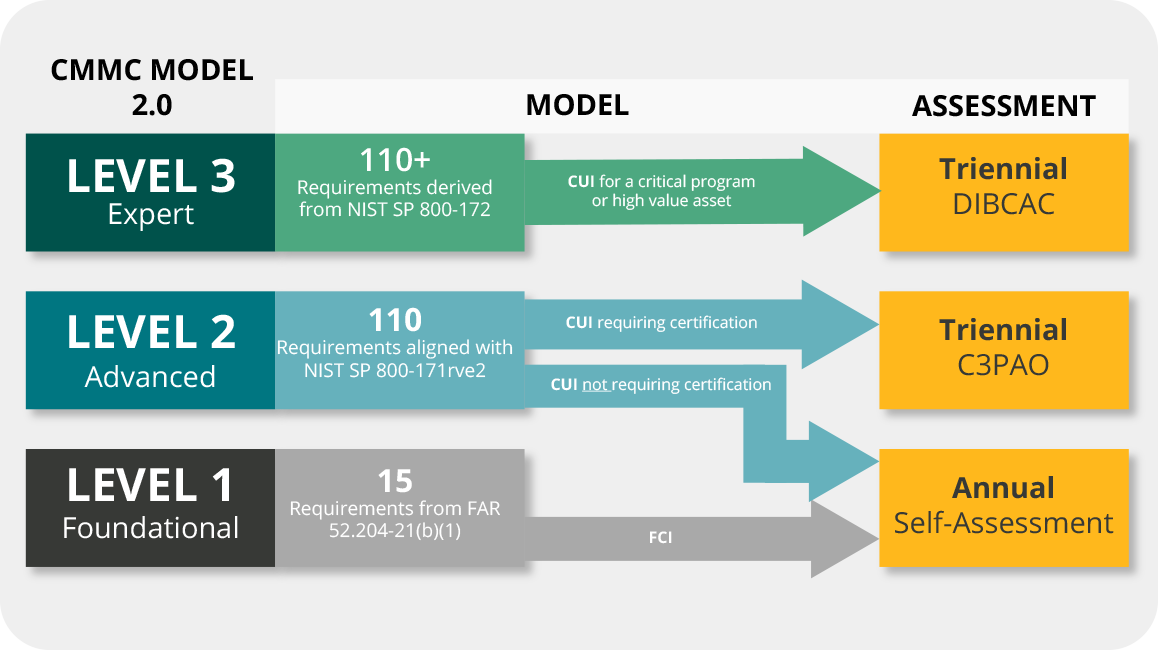
For AEC firms working on federal contracts, achieving compliance means more than just meeting regulations, it’s about safeguarding your business, protecting sensitive project data, and maintaining your eligibility to bid on government work.
The Role of the SPRS Score in Compliance
A crucial component of meeting CMMC 2.0 and NIST 800-171 standards is your Supplier Performance Risk System (SPRS) score. The SPRS score is a numerical representation of your organization’s adherence to NIST 800-171 controls. Before pursuing DoD contracts, contractors must submit their SPRS score, which the government uses to evaluate cybersecurity readiness.
- Higher Scores Provide a Competitive Advantage: A strong SPRS score demonstrates your commitment to cybersecurity and makes your firm a more attractive partner for government projects.
- Low Scores Can Jeopardize Contract Eligibility: A poor SPRS score can disqualify your business from contract awards, even before CMMC 2.0 is fully implemented.
- Regular Updates Are Required: Firms must reassess and update their SPRS score as they implement security improvements, ensuring continuous compliance.
The Risks of Non-Compliance
The consequences of failing to meet CMMC 2.0 standards are severe:
- Lost Contracts: If you’re not compliant, you may be disqualified from bidding on federal projects.
- Financial Impact: Remediation costs can skyrocket if you wait until the last minute to address gaps.
- Reputation Damage: A data breach or non-compliance finding can erode trust with government agencies and partners.
Why You Need to Act Now
Many firms mistakenly believe they can wait to start their compliance journey. However, achieving CMMC 2.0 compliance is a multi-step process that takes time. Here’s why early action is crucial:
- Assessments and Remediation Take Time: Conducting a gap analysis, addressing deficiencies, and implementing new security controls can take 6–12 months or more.
- Third-Party Certification Will Be Required: Unlike previous self-attestation models, CMMC Level 2 requires an independent third-party assessment. Certification bodies will be in high demand as the deadline nears.
- Federal Contracts May Require Compliance Before the Deadline: Some contracts may start including CMMC requirements before November 2025, so waiting could mean missing out on lucrative opportunities.
What Steps Should You Take Today?
Conduct a Readiness Assessment
Identify gaps between your current cybersecurity posture and CMMC 2.0/NIST 800-171 requirements. Then, develop a plan of action and milestones (POAM) to address deficiencies.
Strengthen Your Security Controls
Implement Multi-Factor Authentication (MFA), Endpoint Detection and Response (EDR), and Zero Trust Architecture. Secure your network with continuous monitoring and managed detection response (MDR).
Develop and Maintain Compliance Documentation
Create or update your System Security Plan (SSP); establish incident response and data protection policies, and ensure your SPRS score reflects your latest compliance efforts.
Train Your Team
Conduct cybersecurity awareness training to ensure employees understand their role in protecting sensitive information, implement phishing simulations and security workshops to reinforce best practices.
Engage with Compliance Experts
If you’re unsure where to start, working with specialists who understand government contracting cybersecurity requirements can help streamline your path to compliance.
Next Steps
The November 10, 2025 deadline is closer than you think. Firms that take action now will not only secure their compliance but will also gain a competitive edge in government contracting.
If you’re uncertain about your firm’s cybersecurity standing or need guidance on the next steps, schedule a CMMC/NIST readiness assessment today. Our team specializes in helping AEC firms navigate cybersecurity mandates and can provide the support you need to meet compliance with confidence.
Secure your contracts. Protect your business. Act now.




